Configuring 3Com
Firewall Analyzer supports the following 3Com Firewalls:
Obtaining Log Information
To create a Firewall Analyzer firewall profile, you must specify the log file location.
3Com firewalls do not create a log file. Instead, they direct a log stream to a syslog server which writes the log information to a file.
Note: The ManageEngine Firewall Analyzer Server(s) can be anywhere on the Network.
X-Family Remote SysLog Configuration
To ensure that all the relevant syslog traffic is sent to the Firewall Analyzer, the X-family device needs configuration on several pages of the LSM. Enable remote syslog on the X-Family device, and configure it with the information required to communicate with the Firewall Analyzer Server(s).
- Open a web browser browse to X-family device internal interface.
- Login and navigate to System > Configuration > Syslog Servers.
- Configure all four logs to be sent to the Firewall Analyzer.
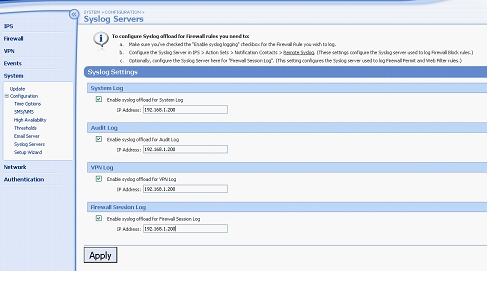
- Click Apply.
- Navigate to IPS > Action Sets > Notification Contacts > Remote System Log and complete the form as shown below.
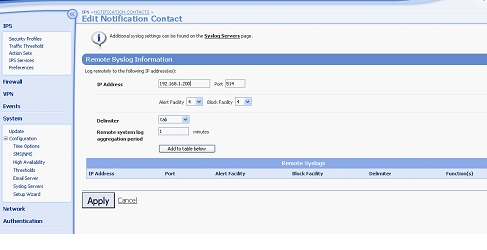
- Click Add to table below.
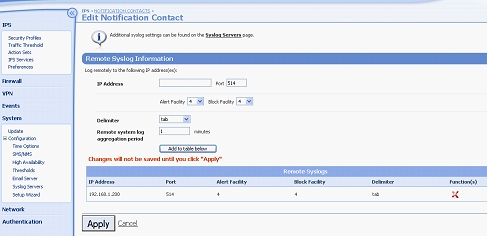
- Click Apply.
- Navigate to Firewall > Firewall Rules and click Create Firewall Rule. Complete the form as shown below.
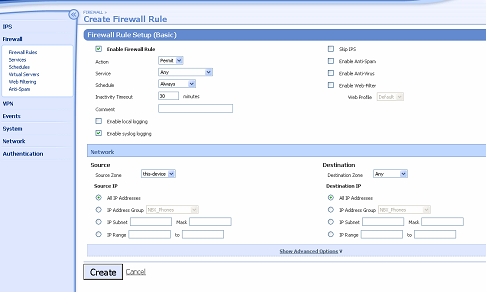
Note that later versions of TOS do not have separate checkboxes for Enable local logging and Enable syslog logging – they just have a checkbox for Enable logging which enables both.
- Click Create. A new rule will be created at the bottom of the table.
- Click Create Firewall Rule. Complete the form as shown below.
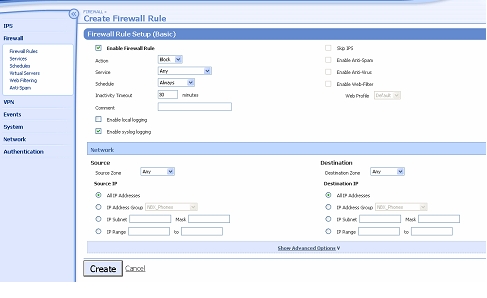
- Click Create. A new rule will be created at the bottom of the table.
Please note that these last two rules must remain the last two rules in the Firewall Rule table. They replace two implicit “hidden” rules that are always present but do not support logging.
- Click the pencil icon next to the first rule in the Firewall Rule table. This will open the rule for edit, as in the example below.
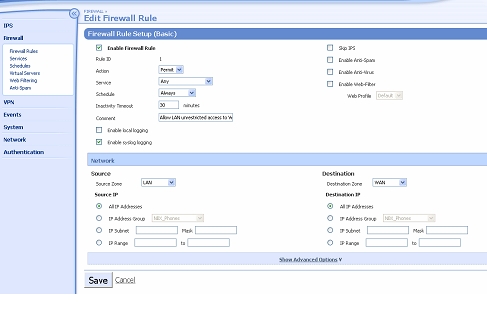
- Click the Enable syslog logging checkbox as shown, then click Save.
- Repeat steps 12 and 13 for all the Firewall Rules until syslog logging is enabled on them all.
Troubleshooting Operation with ManageEngine Analyzer
The Firewall Analyzer home page shows the “Dashboard” which is an overview of all the devices that are being monitored, showing traffic levels and security events that have been reported.
The X-family device should appear here. If it does not, see the troubleshooting section below.
The following is a list of things to check if the ManageEngine Firewall Analyzer does not operate correctly:
- Check the syslog server settings on the X-family device are configured to point to the IP address of the Firewall Analyzer Server.
- Check that the Firewall Analyzer Server is listening on the same port (usually UDP 514) as the X-family syslog client is sending on.
- Check that any firewall device between the X-family and the Firewall Analyzer Server has a rule permitting traffic for UDP port 514.
- Check that there is no syslog daemon running on the same PC as the Firewall Analyzer Server – or it will take over port 514 which will stop the syslog data from going to the Firewall Analyzer Server.
- Traffic through the X-family device will only be counted if it is subject to a Firewall Rule and syslog logging is enabled for that rule. For example traffic will not be counted if:
- it is passing between hosts in the same security zone
- it is passing over a VPN or GRE tunnel to a host which is in the same zone as is used to terminate the VPN or GRE tunnel.
- Events will not be generated for “hidden” firewall rules. At the time of writing, there are two implicit “hidden” firewall rules that are not displayed but act as if they were the last two rules in the Firewall Rule table. These are:
Permit from this-device to ANY zone ANY protocol
Block from ANY zone to ANY zone ANY protocol
These rules do not generate log entries or syslog messages.
To enable the Firewall Analyzer to monitor events that would be generated by these rules, two explicit rules must be created as the last two rules in the Firewall Rule table and syslog logging must be enabled on both of them.
|