Ticketing System Integration
Key Manager Plus integrates with enterprise ticketing systems to automatically create service requests for vulnerable or expiring SSL certificates. The integration ensures that periodic tickets are created in the ticketing system to alert the technicians and take timely action to reduce the security threats posed by expiring or vulnerable SSL certificates. The frequency of service request creation for expiring and vulnerable tickets will be governed by the notification policies set for the same by the user.
- How does the Ticketing System Integration work?
- Steps to integrate ticketing systems with Key Manager Plus
1. How does the Ticketing System Integration Work?
Key Manager Plus allows you to set up periodic notifications, in the form of emails or syslog messages, to check for expiring or vulnerable SSL certificates in the repository.
To enable the ticketing system integration, enter the server URL of the machine where the ticketing system is running, in Key Manager Plus and ensure that the ticketing system host is accessible by the Key Manager Plus server.
Once enabled, Key Manager Plus will create tickets in the ticketing environment automatically, whenever the notifications for expiring/vulnerable SSL certificates are triggered during a scheduled or a manual vulnerability check.
Prerequisite
Tickets are created in the ticketing environment based on the notification policy set for SSL certificates that are expiring and/or deemed as vulnerable in Key Manager Plus. Click here to learn more about how to set up notifications for the same.
1.1 SSL Expiry
The SSL expiry ticket is created as part of the default expiry notifications sent by Key Manager Plus, as well as the scheduled SSL expiry reports. The notifications are triggered whenever a scheduled expiry report or default expiry notification task is run in Key Manager Plus.
- You can set up a schedule for notifications regarding expiring SSL tickets in Settings >> Notification >> Expiry. To enable SSL certificate expiry notifications, select the 'Notify about SSL certificates expiring within' checkbox. Choose a value for days. You will be notified about only those certificates whose expiry dates fall within the period (number of days) you enter. Customize the frequency of the notifications as per requirement. Once the schedule is set, Key Manager Plus will collate a list of expiring certificates falling under the specified number of days.
- For each SSL certificate, Key Manager Plus will check if an expiry ticket is already created in the ticketing environment. If not, a new ticket will be opened. The new ticket will contain details such as the Ticket Number, Status, IP Address, Certificate Serial Number for which the ticket is created locally.
- If a ticket already exists, the status of the ticket will be checked. If the status of the ticket is Open, In Progress, or On Hold, Key Manager Plus will not create a new ticket. However, if the status is Resolved, Canceled, or Closed, Key Manager Plus will re-open the ticket until the corresponding SSL certificate in renewed and updated in Key Manager Plus repository.
- Tickets created by Key Manager Plus will be flagged as 'High Priority'.
1.2 SSL Vulnerability
The SSL vulnerability ticket is created as part of the default schedule for vulnerability scan done by Key Manager Plus, as well as manual scans. A ticket will be created for each vulnerability, detected during the vulnerability scan.
- You can set up a schedule for vulnerability scans in Settings >> SSL >> SSL Vulnerability. Configure the recurrence type to set up the scan to run daily or weekly.
- First, Key Manager Plus will check if a vulnerability ticket already exists in the ticketing environment using the certificate serial number, Domain Name, and IP Address. If a ticket is already created, the status of the ticket will be retrieved.
- If the ticket status is Open, In Progress, or On Hold, Key Manager Plus will simply add the latest scan results to the ticket. If the ticket status is Resolved, Canceled, or Closed, but vulnerabilities are still found in the scan results, then Key Manager Plus will reopen the ticket and add the latest scan results to it.
- If no ticket is corresponding to particular server vulnerability is available in the ticketing environment, Key Manager Plus will create a new ticket.
- In the ticketing system, a separate ticket is created for each domain - IP vulnerability combination. For example, consider a certificate with common name example.com and SAN namely test.example.com, used for two different IP addresses as follows: If vulnerabilities found at both locations, then two tickets will be created for example.com@192.168.0.23 and for test.example.com@192.168.205.35. Even though the certificate used is the same, since the servers locations are different, they will be considered as two different vulnerabilities.
- Tickets created by Key Manager Plus will be flagged as 'High Priority'.
Note: The vulnerability tickets will only contain details of weak ciphers found during the scan i.e., the ticket will not list the health of other ciphers available in that particular server if they are not found to be vulnerable.
2. Steps to Integrate Ticketing Systems with Key Manager Plus
Listed below are the ticketing systems currently supported by Key Manager Plus:
- ServiceDesk Plus (on-premise)
- ServiceNow
2.1 ServiceDesk Plus
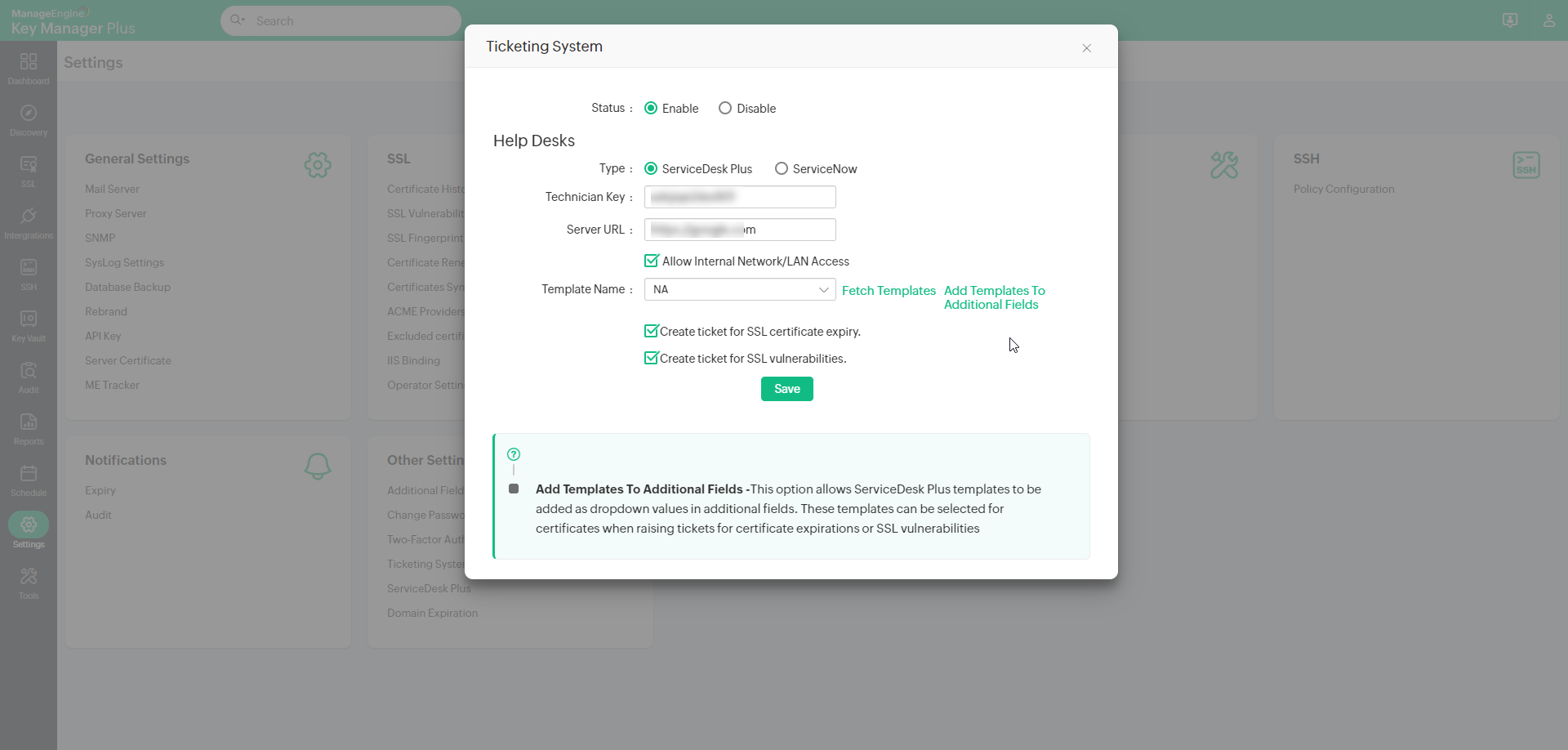
- Navigate to Settings >> Ticketing System and choose Enable
- Under Help Desks, click ServiceDesk Plus
- Enter the ServiceDesk Plus Technician Key (API Token) and Server URL where the ServiceDesk Plus host is running.
- Select the Template Name.
[or]
Click Fetch Templates to bring in all the available templates from ServiceDesk Plus. Now, select a template that contains default fields while ensuring that it does not have any mandatory custom fields, failing which will fail ticket creation. - Under Create Tickets, select Create ticket for SSL certificate expiry or Create ticket for SSL vulnerabilities or both, based on your requirement. Click Save.
Format for SSL Expiry tickets in ServiceDesk Plus
Subject: SSL Certificate <common name> expiry
Description:
The SSL Certificate <common name> expiring soon, please take care
Common Name:<common name>
Expiry Date: Feb 25, 2020
Scanned by: Key Manager Plus running at https://<kmpserverurl>:<port>
Format for SSL Vulnerability tickets in ServiceDesk Plus
Subject: Vulnerabilities for <domain name>
Description:
<Domain Name>(this could be the SAN)
<Common Name> (certificate common name)
<IP Address>
Weak ciphers in use, which should be removed
<Names of the ciphers found to be weak>
If any vulnerabilities such as OCSP, CRL, HeartBleed, or Poodle are found, then the corresponding Signature Algorithm and expiry date information will also be added here.
Scan Time
Scanned by: Key Manager Plus running at https://<kmpserverurl>:<port>
2.2 ServiceNow
- Navigate to Settings >> Ticketing System and choose Enable.
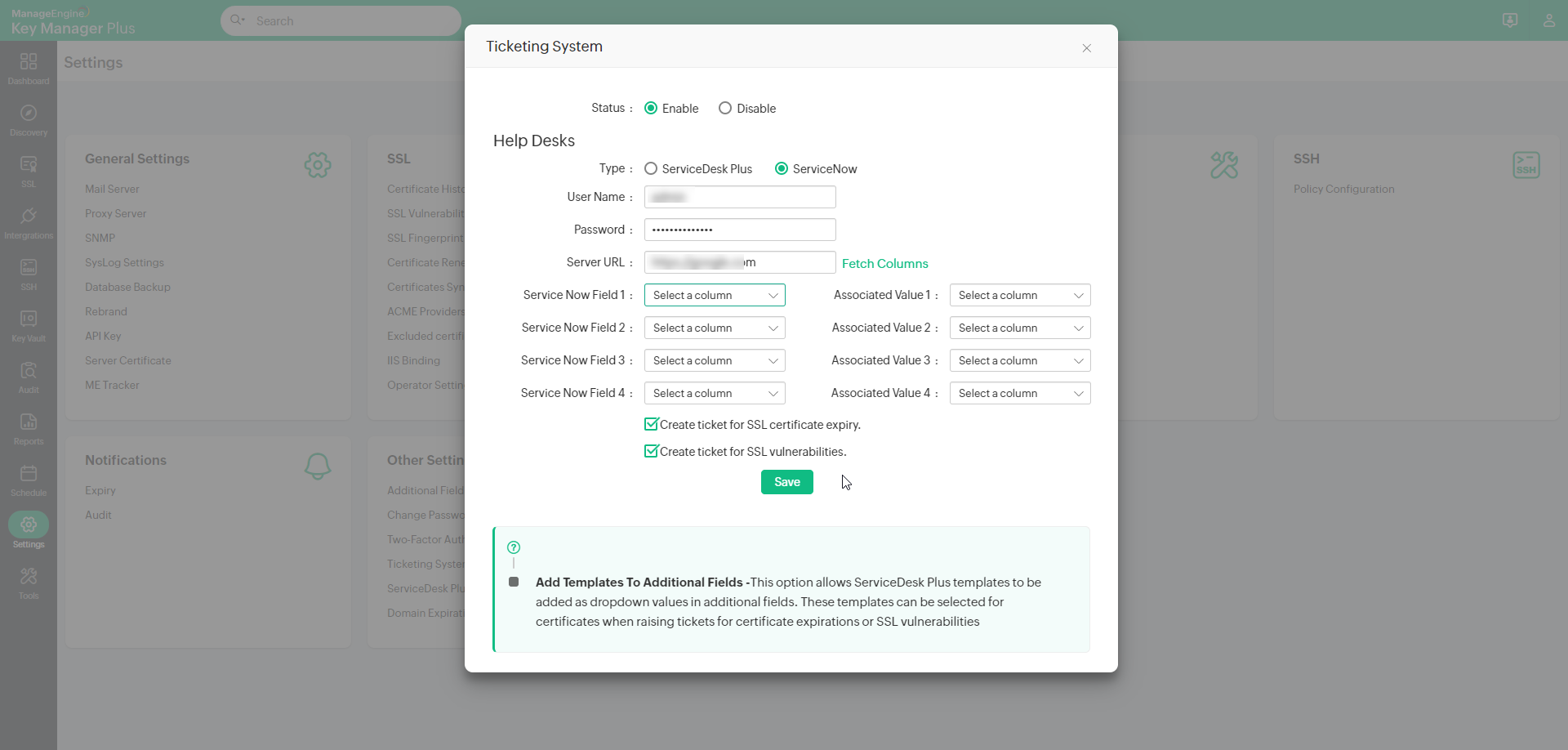
- Under Help Desks, click ServiceNow.
- Enter the ServiceNow User Name, Password, Server URL where the ServiceNow host is running.
- Click to Fetch Columns from ServiceNow. The fetched columns will be displayed under additional fields. Now, select the fetched columns from additional fields and associate it with an existing column in Key Manager Plus. This allows users to add additional information to the tickets created in ServiceNow.
- Under Create Tickets, select Create ticket for SSL certificate expiry or Create ticket for SSL vulnerabilities or both, based on your requirement. Click Save.
Format for SSL Vulnerability tickets in ServiceNow
Short Description: SSL Certificate <common name> expiry
Additional Comments:
The SSL Certificate <common name> expiring soon, please take care
Common Name:<common name>
Expiry Date: Feb 25,2020
Scanned by: Key Manager Plus running at https://<kmpserverurl>:<port>
Format for SSL Vulnerability tickets in ServiceNow
Short Description: Vulnerabilities for <domain name>
Additional Comments:
<Domain Name>(this could be the SAN)
<Common Name> (certificate common name)
<IP Address>
Weak ciphers in use, which should be removed <Names of the ciphers found to be weak>
If any vulnerabilities such as OCSP, CRL, HeartBleed, or Poodle are found, then the corresponding Signature Algorithm and expiry date information will also be added here.
Scan Time
Scanned by: Key Manager Plus running at https://<kmpserverurl>:<port>