Direct Inward Dialing: +1 408 454 4213
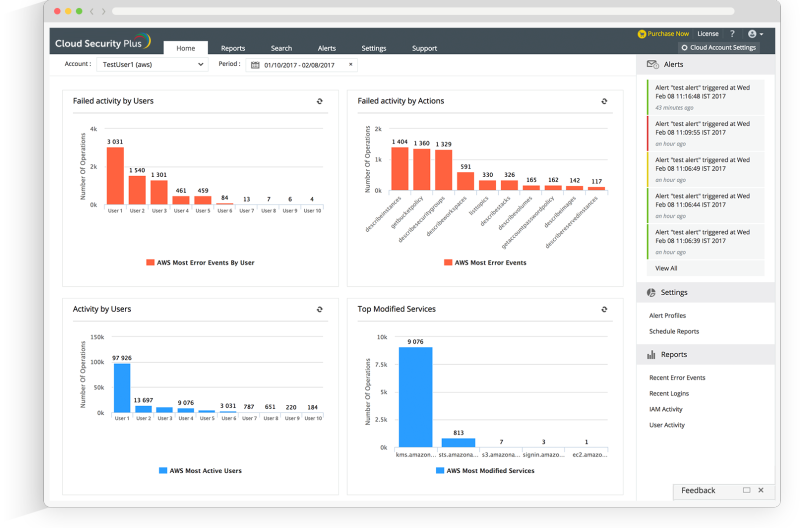


Securing AWS Cloud platform
Cloud Security Plus collects, monitors, and analyses the log data from AWS cloud platform and provides out-of-box reports and alerts for the same.
Securing Azure cloud platform
Collect, monitor, and analyse log data from Azure environment
Salesforce log management
Cloud Security Plus fetches Salesforce event logs from Salesforce Event Monitoring through REST API calls to monitor login, report, content, and search activity. This can help in the proactive monitoring of critical events in your Salesforce environment.
Google Cloud Platform log management
Get detailed insights on user activity, IAM, network security, VPC activity, network services, cloud functions, App Engine, Google storage, and GCP resource management with extensive log retrieval using gRPC calls.
Your download is in progress and it will be completed in just a few seconds!
If you face any issues, download manually here